Cloud-First Doesn’t Mean Threat-Proof
In our latest Cloud Cuts episode, Eon Co-founder Gonen Stein sits down with Mansi Vaghela, a Senior Partner Solutions Architect at AWS, for an unfiltered conversation about the modern ransomware threat – and how to stay ready.
With ransomware attacks escalating across industries and cloud adoption continuing to rise, this is a must-listen episode for security leaders and cloud teams alike.
Want to hear how AWS thinks about ransomware recovery?
👉 Watch the full episode
Let’s walk through some key insights from the session.
The Growing Threat of Cloud Ransomware
Ransomware has become one of the most common and damaging cybersecurity threats businesses face today. As early as 2021, Gartner predicted that 75% of IT organizations would face one or more ransomware threats by 2025. The potential financial cost? Up to $20 billion annually.
“Ransomware isn’t a rare thing anymore. It’s happening constantly. From major hotel chains like MGM to healthcare providers like Scripps Health, so many businesses across different industries have been hit.”
— Mansi Vaghela, AWS, Senior Partner Solutions Architect
Beyond the financial ransom itself, the long tail of damage lies in prolonged downtime, regulatory fallout, and reputational harm.
For cloud-first companies, the risks are amplified. With critical data backups distributed across dynamic environments and no physical perimeter to protect assets, a single compromised credential or misconfigured permission can trigger a chain of events that takes entire operations offline, locks teams out of their own data, and incurs steep recovery costs. In cloud environments, attackers often gain access by exploiting long-lived credentials and excessive permissions, reminders of just how essential identity and access management has become.
How AWS Hardens the Cloud Against Ransomware
One of the central themes of Gonen and Mansi’s conversation is the importance of guidelines like the NIST Cybersecurity Framework in helping companies structure their approach to cyber defense.
AWS, Mansi explains, always strives to offer the powerful tools that their customers need to align with the NIST Cybersecurity Framework. From automated patching and Blue-Green deployment architectures to credential management using AWS Secrets Manager and Systems Manager (SSM), AWS delivers baked-in benefits that reduce the manual lift traditionally required to stay secure.
The conversation also goes into depth on AWS’s “multi-layer approach” – a comprehensive strategy that includes strong access controls, network segmentation, encryption, and continuous monitoring. Implementing least privilege access across accounts and regions plays a critical role in this approach, helping prevent hackers from achieving lateral movement through an organization's cloud architecture in the event of a breach.
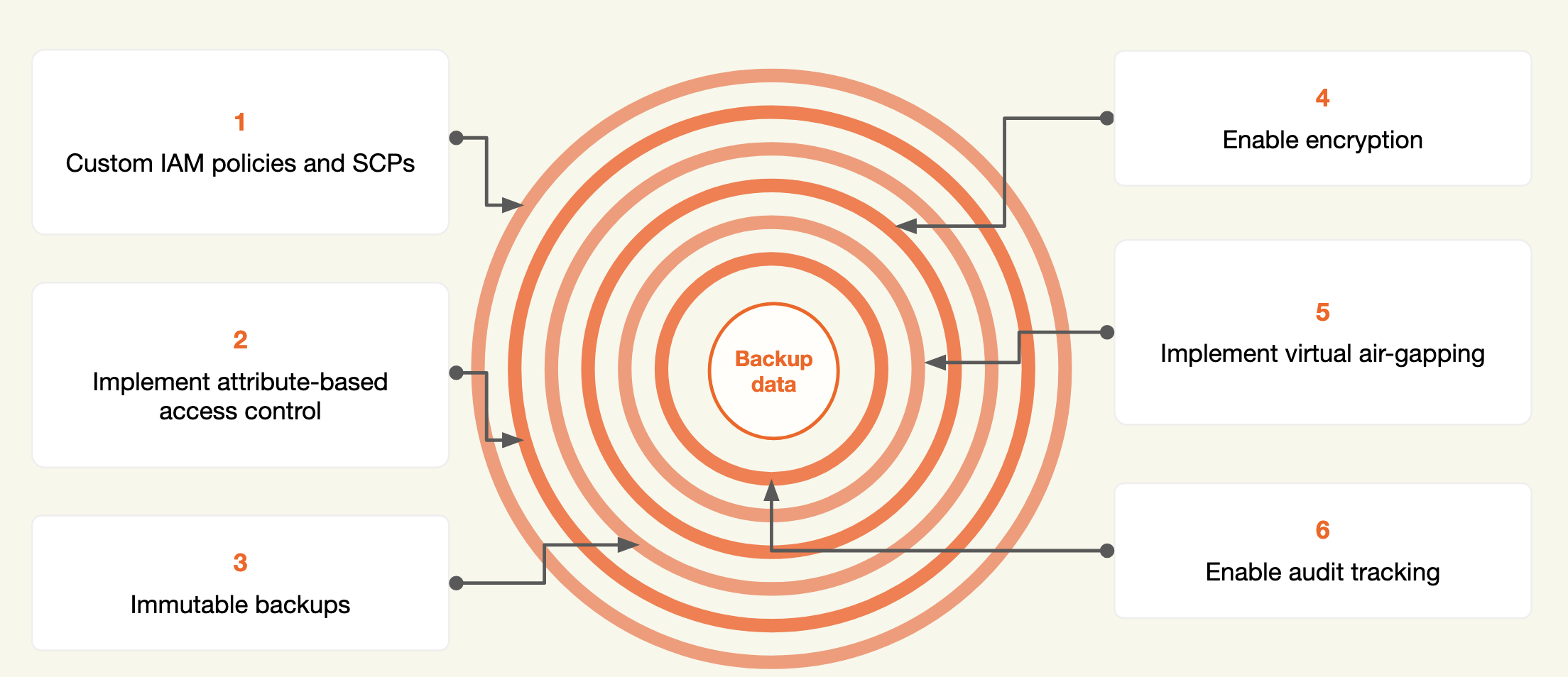
And if an attack does happen? AWS provides layered support, including incident response playbooks, real-time logging via CloudTrail, threat detection through Amazon GuardDuty, and a robust ecosystem of solutions partners, including Eon.
Building Strong Ransomware Backup & Recovery
But what happens when attackers succeed in locking organizations out of their data? Here, backup protection and recovery become a business-critical function, not just a technical one.
“[A] strong backup and recovery strategy can mean the difference between a quick recovery and a major disruption. A backup is only effective if you can restore it when needed. That’s why it’s crucial to establish well-documented backup and restore processes.
— Mansi Vaghela, AWS, Senior Partner Solutions Architect
The key lies in regular testing and validation. Accordingly, AWS recommends that companies undergo frequent testing and validation of backup recovery procedures to ensure that data can be retrieved without corruption or delays. If an organization hasn’t tested its restore process in six months, it is time to start. Backups that aren’t verifiable as being up to date aren’t backups. They’re just assumptions.
Another critical point from the session is that backing up data doesn’t make it inherently secure – you have to secure the backup environment itself. Mansi emphasizes the importance of air-gapped or logically isolated backups that malicious actors cannot access or overwrite during an attack. This is where the concept of a “secure backup account structure” comes in – ensuring that even if data production environments are compromised, backed-up data remains untouched and recoverable.
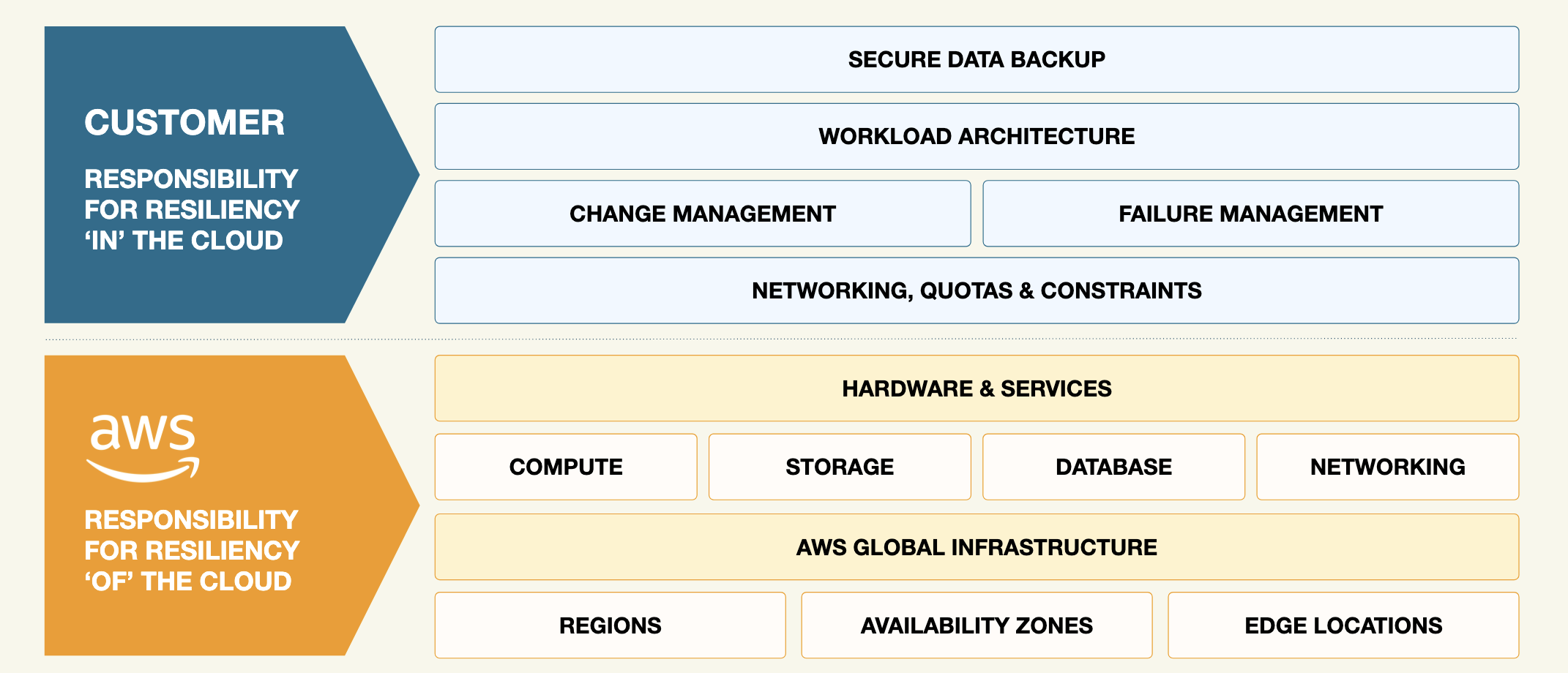
As they build backup and recovery strategies, too many companies overlook the gap between infrastructure security and data protection, referred to as the "shared responsibility model." Companies can trust their cloud vendor to manage the security of the cloud, but customers are responsible for the security of what they’ve stored in the cloud.
“Think of it like this: If you’re renting an apartment, AWS is responsible for securing the building, but you still need to lock your own doors.”
— Mansi Vaghela, AWS, Senior Partner Solutions Architect
AWS ensures the infrastructure is sound, but customers are responsible for managing data access, permissions, and backup integrity. And in the case of cloud data protection, “locking your doors” takes more than a key – it’s a responsibility that includes exacting granular control over user permissions, monitoring anomalies, and ensuring backups are safely stored and recoverable.
How Eon Automates NIST-Aligned Backup Protection
Many customers find that managing security responsibilities in the cloud, especially backup management, is far from straightforward. Cloud environments are dynamic, resources are spun up and down constantly, and traditional backup tools, often designed for on-prem environments, simply can’t keep pace.
Eon’s end-to-end ransomware package was built precisely to fill this gap.
It's not a bolt-on feature or a set of generic scripts. It's a fully integrated part of Eon’s Cloud Backup Posture Management (CBPM) platform – a system that continuously assesses, adjusts, and optimizes backups in real-time.
Eon Snapshots, which are Eon’s purpose-built backup storage tier, allow instant access to data backups and granular restores, including file-level and row-level recovery for structured data. That means teams can recover exactly what they need—faster and cheaper—without the overhead of full snapshot restores.
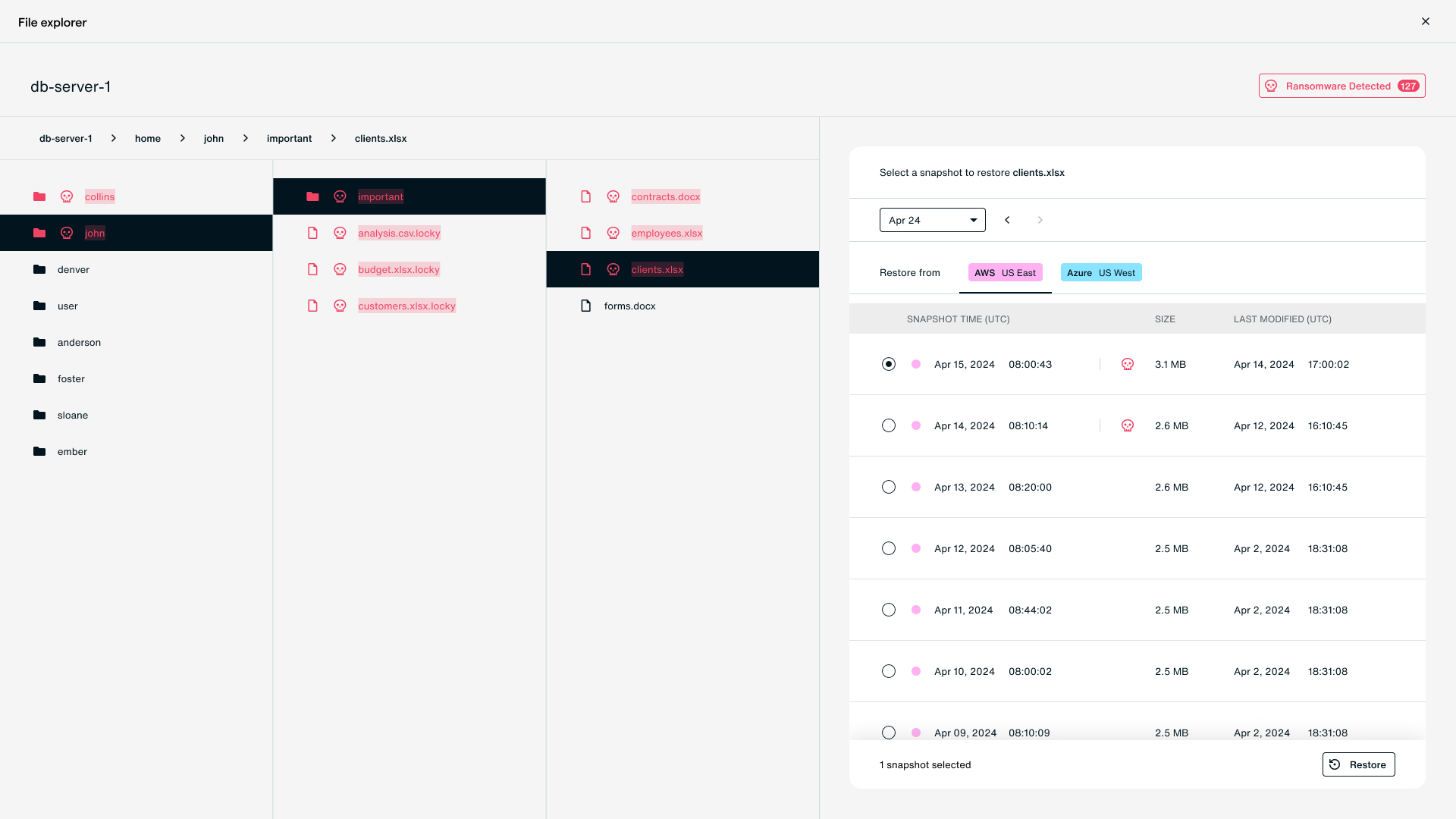
Eon continuously discovers and classifies resources to ensure backup policies remain aligned with your live cloud posture—eliminating “backup drift” and protecting newly created assets automatically. It also helps teams cut through cloud sprawl by decommissioning backups for obsolete resources.
What makes Eon unique is its awareness of the data inside the cloud—not just the infrastructure around it. Eon can proactively detect ransomware’s impact across both structured data (like database records) and unstructured data (like files in object storage or virtual machines). That visibility means faster detection, clearer scope, and smarter recovery.
And when it comes to ransomware, Eon’s platform aligns directly with the NIST Cybersecurity Framework, covering all five pillars:
- Identify: Continuously scans cloud environments to ensure all critical data is backed up and policy-aligned.
- Protect: Uses air-gapped, immutable storage to keep backups isolated and safe from ransomware.
- Detect: Monitors backups for ransomware signatures like entropy changes and suspicious file activity.
- Respond: Provides a unified view and role-based tools to investigate, scope, and plan a recovery.
- Recover: Enables fast, targeted restore of compromised data—no need for full snapshot recovery of clean data (without the risk of bringing back compromised data).
Eon also delivers this protection in a cost-effective way. Because it performs incremental backups and scans, Eon avoids the overhead of full data scans or full snapshot restores—unlike many detection tools that require a complete rescan every time. That means teams get continuous protection and insight, without continuously spiking their cloud bill.
Article: Complete Guide to Protecting Your Cloud Environments from Ransomware
The Blueprint for Cloud Ransomware Resilience Starts Here
The threat of ransomware isn’t going anywhere. If anything, it’s evolving faster than many organizations’ ability to adapt. That’s why security leaders today must craft a proactive ransomware protection strategy that is concerned not just with preventing attacks but also with building infrastructure ready to recover from them.
The insights from this Cloud Cuts episode offer a blueprint for doing exactly that. Whether it’s enforcing stronger credential management, separating backups from production environments, or adopting automated posture management tools like Eon, the takeaway is clear: resilience isn’t optional.
It’s the new baseline.
🎧 Listen to the full Cloud Cuts episode on Ransomware
Featuring:
• Mansi Vaghela – Senior Partner Solutions Architect, AWS
• Gonen Stein – President & Co-Founder, Eon
Register for the next episode of Cloud Cuts Live: How to Cut Cloud Data Retention Costs









.jpeg)
